Introduction: What’s USB Armory Bundle?
In recent years we have witnessed enormous success of credit card sized computers like Raspberry PI. They are cheap, affordable, versatile and fully customizable. Versatility and customization of such devices led to its expansion into various specialized fields of computer and software engineering. And that trend led us to USB Armory bundle.
USB armory bundle is a flash drive sized computer. It is manufactures by Inverse Path & F-Secure. Carried by open source philosophy it board hardware design is fully customizable. Enables user to develop and run personal security applications on wide range of standard software environments.

USB Armory Bundle: How it works?
However, it boasts very powerful hardware for a such tiny device. Depending on model you buy, you can have in your arsenal ultra-efficient but very powerful NXP i.MX53 or NXP i.MX6UL/i.MX6ULZ ARM® Cortex™ SOC module which by itself is complete development platform for both evaluation and application development purposes:
Moreover, after the secure booting finishes now you have the most secure hardware and software environment that can fit in your back pocket. What can you do with it? Well the most obvious thing you can do is to write security applications of your own.
USB Armory Bundle [features, hardware specs, design]
Much of the USB Armory security features comes with SOC module like:
- Secure boot, High Assurance Boot with digital signature, Secure Non-Volatile Storage, including Secure Real Time Clock, Security State Machine, Master Key Control, and Violation/Tamper Detection and reporting, BUS encryption engine and ARM Trust zone.
Additional level of hardware protections comes in the form of two external microchips for additional hardware acceleration for cryptography, encryption and hardware based key storage. Microchips provide high-endurance monotonic counters, useful for external verification of firmware downgrade/rollback attacks.
Connectivity is also obtained through SOC module. Options are:
- USB emulation on plug and receptable, TCP/IP via Ethernet over USB, flash drive emulation, serial communication over USB or physical UART as a part of hardware integrated circuit, mass storage emulation as a standard USB flash drive, Mouse/Keyboard emulation via USB Human Interface Device (HID) Gadget, serial download protocol (SDP) used to directly download and execute code on the SoC.
MKII version of USB Armory on top of all available connectivity options in MKI has a Bluetooth module.
Features:
- File encryption, decryption, data self-destruct
- Malware scanning
- Random Number Generator
- Personal, client-side digital wallet system for online and real world micropayments, bitcoin wallet
- OpenSSH client and agent for untrusted hosts
- Symmetric and asymmetric key encryption, message signature, signature verification, hashing
- Full password manager with integrated web server, user password generation and verification
- Hardware security module (HSM) for physically safeguarding and managing digital keys, key generation, key storage, key authentication.
- Token verification, authentication, creation and licensing
- Management of database keys or even keys for storage devices
- Symmetric and asymmetric (public-key) cryptography, GPG server
- USB firewall.
- Penetration testing platform, low level USB security testing
- Router for VPN tunnelling, Tor
Components:
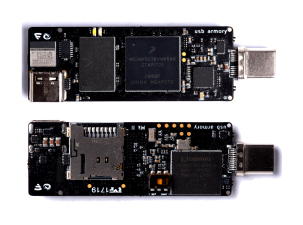
Inverse path produces USB Armory bundle in two versions: USB Armory MK I and MK II.
MK I version boasts with:
- NXP i.MX53 ARM® Cortex™-A8 800Mhz, 512MB DDR3 RAM
- USB host powered (<500 mA) device with compact form factor (65 x 19 x 6 mm)
- ARM® TrustZone®, secure boot + storage + RAM
- microSD card slot
- 5-pin breakout header with GPIOs and UART
- customizable LED, including secure mode detection
- excellent native support (Android, Debian, Ubuntu, Arch Linux)
- USB device emulation (CDC Ethernet, mass storage, HID, etc.)
- Open Hardware & Software

MK II version carries:
- NXP i.MX6UL/i.MX6ULZ ARM® Cortex™-A7 900Mhz, 512MB/1GB DDR3 RAM
- Cryptography co-processor drivers: DCP (i.MX6ULZ), CAAM (i.MX6UL)
- USB host powered (<500 mA) device with compact form factor (65 x 19 x 6 mm)
- ARM® TrustZone®, secure boot + storage + RAM
- Secure elements Microchip ATECC608A and NXP A71CH
- internal 16GB eMMC + external microSD
- u-blox ANNA-B112 Bluetooth module
- debug accessory support for UART, GPIO, SPI, I²C, CAN breakout
- customizable LEDs, including secure mode detection
- supported by vanilla Linux kernels and distros
- USB device emulation (CDC Ethernet, mass storage, HID, etc.)
- Open Hardware & Software
Conclusion
Inverse path cleverly built USB Armory around NPX SOC module which by itself is armed with multitude of security features. Features built into NPX SOC and ARM cpus in general are core of this device on which creatice user can build multitude of security applications and environment. With respectably powerful CPU for such a small device USB Armory can be used in variety of security situations and puposes ranging from key generation, validation, storage, authemtication and more demanding situations like VPN tunnelling and SSH client.

![Packet Squirrel [Hak5] Packet Squirrel [Hak5]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/03/packet_squirrel_bg-500x275.jpg)

![BladeRF 2.0 micro [Nuand] BladeRF 2.0 micro [Nuand]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/03/bladeRF_2_0_micro_bg-500x275.jpg)